Since the start of the pandemic, cybercrime has been booming.
In 2020, cases of online identity theft doubled, and malware attacks increased by 358%. There is now a ransomware victim every 10 seconds, opening their laptop or phone to find their data encrypted and held hostage by hackers.
In total, cybercrime cost companies and private individuals over $1 trillion last year.
With cases rising and hacking attacks becoming ever more sophisticated, what can you do to protect yourself and your data?
Here’s a detailed run-down of seven crucial steps to follow to protect yourself against rising cybercrime.
1 – Check if You Have Already Been Compromised
It’s possible that some of your data – or even your identity – has been stolen without you knowing.
Often, it takes weeks or even months before you notice anything after a cybercriminal gets hold of your personal data or some of your passwords. It mostly depends on whether the hackers are out to make a profit quickly, or whether they hold onto your information to resell it.
Sooner or later, though, the signs start piling up – bills for services you did not order, and payments you didn’t authorize are just the beginning.
To avoid this, check preemptively whether your data has been compromised.
Here is a quick guide on how to do this:
- Round up all email addresses you have used to sign up for online services or subscriptions.
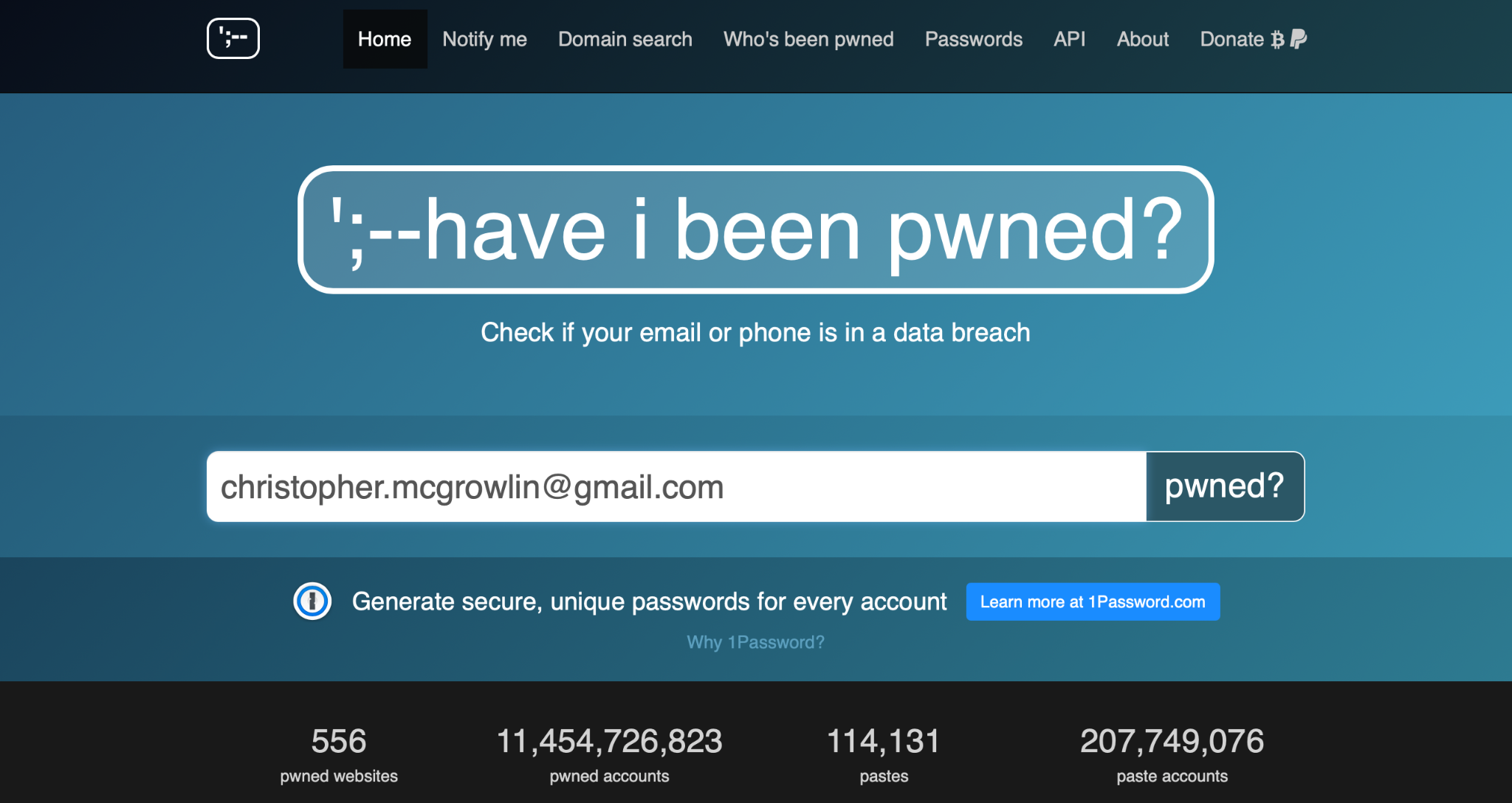
- Use a free online service like Have I Been Pwned. Here, you can compare your email addresses against those involved in known data breaches. Often, identity theft is the result of a major company being hacked, and customer data being leaked. Over the past decade, over 10 billion records have been compromised that way.
- Enter your email address and click the “pwned?” button.
- If your email doesn’t match any that has been affected by known breaches, you’ll get a green “Good news!” notification.
- Otherwise, you’ll receive a red notification informing you that your account has been compromised – and in which data breaches it happened.
- Haveibeenpwned.com is free to use, but you have to check each email address individually and manually. For increased protection, subscribe to a service that automatically monitors your information.
2 – Upgrade Your Passwords and Use a Password Manager
Everyone’s heard this one before. Yet, 80% of data breaches are still due to weak passwords.
This doesn’t just concern personal accounts, either. The Colonial Pipeline breach in April 2021, for example, resulted from poor password maintenance. Ultimately, a single compromised password caused fuel shortages along the entire East Coast.
Here’s how to audit your passwords and increase your security:
- Use unique passwords for all of your accounts – never use the same for multiple accounts.
- A strong password is complex: at least 12 characters long, with uppercase and lowercase letters, numbers, and special symbols. It should also not be part of your personal information. Avoid using names of people and places or dates of important life events.
- Consider using a password manager. These tools store all your passwords for you, and you only have to remember a single master password. Many password managers alert you to vulnerabilities like weak or duplicate passwords.
- Enable two-factor authentication (2FA) where you can. With 2FA logins, you prove your identity with a separate device, usually your phone. You might get texted a code or confirm it’s you in an app when anyone logs into your account. This means that hackers can’t access your information without also having your physical device.
3 – Boost Security on Your Home Network
As a next step, go over all your hardware to make sure that maximum security settings are enabled. Often, cybercriminals use stolen and weakly secured phones, or even your home Wi-Fi to get at your sensitive data.
Secure your home router first. This controls all incoming and outgoing traffic from your home Wi-Fi – the network where, most likely, you’re handling your most personal transactions.
- Set up a complex router password, according to the specifications in the last step, and be careful who you share it with. Change your password regularly in case one of your family members or regular visitors becomes compromised.
- Modify your router’s admin credentials – both the username and the password. Many models come with weak default settings, starting with the admin username simply being “admin”. However, anyone who has access to these credentials can change the configuration of your home network.
- Use strong Wi-Fi encryption: Enable Wi-Fi Protected Access 2 (WPA 2) in your settings. In many cases, it’s also possible to give it another boost by using the AES Cipher settings in the advanced menu.
- Turn off Wi-Fi Protected Setup (WPS), which allows devices like game consoles to stay connected to your network, even when you change your password. It’s also a weak spot that hackers often exploit.
- Change your network’s SSID – that’s the name it appears under in your computer’s Wi-Fi settings. By default, many networks will be displayed as the name of your provider, followed by a number. However, this makes life easier for hackers because they can handily identify the router’s software configuration. Instead, change the name of your network to something more obscure. Don’t use your family name or home address. Certainly don’t issue a challenge to hackers along the lines of “Youcanthackme123”
- Hide your network. Often, it’s possible to stop your SSID being publicly broadcast. Any devices that are already in the network will stay connected. But new ones won’t be able to find – or hack – it.
- Regularly update the firmware of your router. In theory, this should be done automatically by the manufacturer, but it’s best to check periodically.
4 – Increase Security Settings on Your Devices
Next, go over your phone, tablet, laptop, and other smart devices like watches, to make sure that your digital security stays intact, even if they fall into the wrong hands.
- Make sure that your passwords are unique and complex.
- Enable encryption on all your devices.
- Switch on “find my device” features where possible, in case you lose one of your devices, or it is stolen.
- Enable remote wipe settings. As a last resort, this allows you to remotely delete data off stolen or lost devices.
- Install digital security programs such as antivirus and VPN (virtual private networks). VPNs are especially important if you’re frequently using public networks, such as at libraries, on public transport, or in coffee shops. They’ll make sure that all your transactions are fully encrypted – and that your financial data won’t fall victim to the hacker slurping a frappuccino one table over.
One other essential thing is to keep your devices updated – both in terms of operating systems and apps. In most cases, cyber criminals don’t bother to look for new weak spots to hack a target. Instead, they exploit known vulnerabilities that have long been fixed by development teams in updates that users might not have installed yet.
5 – Invest in Digital Security Products
Digital security products have already cropped up a few times in this guide. Now, it’s time to deep-dive into what software you need to invest in to stay safe in the face of rising cybercrime.
There’s a huge number of cybersecurity providers out there, all of them offering various components that can increase your digital security. To comprehensively protect yourself, you need these features:
- Antivirus and malware protection to root out malicious programs that might have ended up on your computer one way or another.
- A firewall to monitor communications between your computer and others. It will help you block attempts at unauthorized traffic.
- VPN to help you browse anonymously online, especially in public networks.
- A password manager to generate and store secure passwords.
In 2021, though, modern cybersecurity is far more comprehensive than these basic features. There are several additional services you can consider to better protect yourself. These include:
- Automatic cloud backups to store your sensitive files in a secure, encrypted folder online. If your information does get stolen, or you become the victim of a ransomware attack, you will at least have backups.
- Hardware monitoring services. These programs will keep track of your devices and will flag attempts by cybercriminals to access your camera or microphone, for example.
- Identity theft monitoring. As mentioned above, you can automate the process of checking whether any of your data has been involved in major known breaches. Additionally, some providers offer dark web monitoring. This means they deploy algorithms based on artificial intelligence to crawl through the seedier corners of the web to check if any of your information is floating around there.
- Credit monitoring services. Providers of these services automatically check with major credit bureaus to monitor them for abrupt credit rating changes, which may indicate a case of identity theft.
In addition, you should consider getting cybersecurity and identity theft insurance. As the name suggests, this type of insurance will help you if you do fall victim to a cyberattack. If you are affected by identity theft, for example, the insurance will typically take care of legal fees, and help you recover afterwards.
When you’re thinking about which platforms to use for the services above, there are two main things to consider: How many different providers you opt for, and how much you will be paying.
In general, it’s better to stick to as few different providers as possible. Yes, some companies are highly specialized in providing one service – such as password monitoring. However, many of the currently available digital security packages are very comprehensive. That means you might end up paying double for several features from different providers.
Instead, paying for a slightly more expensive subscription from a single provider can centralize all the different digital security elements on this list. It will also help you save money in the long run. Big providers like Norton, Kaspersky, and Avira now provide packages including all essential elements. Some newer players, like Aura, even offer identity theft insurance as part of the deal.
When you’re considering pricing options, keep in mind that having your identity stolen is far more expensive than any subscription. Collectively, US consumers lost $56 billion to identity fraud in 2020. And on an individual level, it can take months or even years of agitation and fraught nerves to recover from an attack.
6 – Talk to Your Family Members about Cybersecurity and Minimize Online Exposure
Once you’ve covered the technical side of cybersecurity, it’s time to consider the human elements. Most successful cyberattacks rely on mistakes people can easily make if their awareness of digital security isn’t up-to-date.
Talk to your family and agree on cybersecurity standards for your home. Ask your family members to go through the same digital security audit of their accounts, and make sure that your collective information is safe.
Especially if you have children, talking to them about cybersecurity is crucial. Since the dawn of remote learning in particular, children have been spending countless hours online every day. It might be tempting to think that, as digital natives, they’re more aware of how the online world works than the adults around them.
However, cyber criminals are increasingly targeting children to steal their personal information, using gaming apps and social media. Giving your kids the run-down on how to spot attacks online is crucial.
One thing that also factors into this are your family’s social media accounts. Often, the information that parents post publicly about their children is enough for cybercriminals to commit identity fraud.
To stay safe, turn on the privacy settings on all your accounts, and on those of your family members. Be clear about what information must not be shared online – on social media or anywhere else. That way, you can prevent sensitive information being harvested off your Facebook profile.
7 – Keep Up With Recent Scams and Learn To Recognize Them
The final step to protect yourself against rising cybercrime is to know what different types of cyber attack actually look like.
For example, phishing scams these days have become much more sophisticated than the “classic” spiel in which a stranded Nigerian prince asks for assistance in return for a generous reward.
Instead, cybercriminals deploy elaborate social engineering scams to get confidential information. You might get an unexpected message from a “friend” with a file to download. Or a request from “Netflix” to quickly verify your account information because it would otherwise be locked. Or it might be your “boss” urgently demanding your assistance.
If you receive any messages along these lines, there are several steps you should run through before you take action:
- Stay calm. Feeling a spike of panic is normal when you read that your account is about to be suspended. But that’s exactly the effect that cyber criminals count on. If a message you receive uses high-pressure tactics or tells you to act right now, take a deep breath and slow down.
- Next, do some background research. Check the sender information. Often, an email claiming to be from your bank or an online subscription service was sent by someone entirely different. A single click on the sender’s address can usually reveal that.
- Even if an unexpected mail is from someone you know, be suspicious. These days, account hijacking is common. It’s possible that a friend’s or coworker’s social media profile or email account has been commandeered by hackers who are now using it to send out messages.
- Don’t click on links. Instead, hover over them to see where they would lead you. Similarly, don’t download any files unless you know the sender and are expecting their message.
- If you get a suspicious message, copy it into a Google search and see if it’s a scam that has been used on others.
Finally, it’s also a good idea to check online cybersecurity news outlets from time to time. Places like The Hacker News, Infosecurity Magazine, and Security Weekly are great to stay up to date with evolving scams and the latest tips to protect yourself.
Conclusion
Cybersecurity is not something you do once and tick off your to-do list. Instead, you have to maintain constant vigilance to stay on top of things and avoid a serious – and costly – breach.
In the face of rising rates of cybercrime, this vigilance is more important than ever.
By following the tips above, you’ll be able to set up a comprehensive system to protect yourself and your loved ones from digital threats.